Difference Between Uploading a Packet and Downloading Packet Wireshark
If you find yourself troubleshooting network issues, and you have to inspect individual packets, y'all need to apply Wireshark. Wireshark is the de facto, go-to, you-demand-to-know-how-to-use, application to capture and investigate network traffic.
Since Wireshark is the exist-all-finish-all tool for this job, let'due south go over some nuts – similar where to download, how to capture network packets, how to employ the Wireshark filters, and more than.
Become the Complimentary Pentesting Active
Directory Environments eastward-book
- What is Wireshark?
- How to Download Wireshark
- Data Packets on Wireshark
- Wireshark Filters
- Additional Wireshark Features
- Wireshark Resource
What is Wireshark?
Wireshark is an open-source network protocol analysis software program started by Gerald Combs in 1998. A global organization of network specialists and software developers back up Wireshark and continue to make updates for new network technologies and encryption methods.
Wireshark is absolutely safety to use. Government agencies, corporations, non-profits, and educational institutions use Wireshark for troubleshooting and educational activity purposes. There isn't a better style to acquire networking than to look at the traffic under the Wireshark microscope.
In that location are questions about the legality of Wireshark since information technology is a powerful packet sniffer. The Low-cal side of the Force says that you should only use Wireshark on networks where you have permission to inspect network packets. Using Wireshark to expect at packets without permission is a path to the Dark Side.

How does Wireshark work?
Wireshark is a packet sniffer and analysis tool. It captures network traffic on the local network and stores that data for offline analysis. Wireshark captures network traffic from Ethernet, Bluetooth, Wireless (IEEE.802.11), Token Ring, Frame Relay connections, and more than.
Ed. Note: A "packet" is a single message from whatever network protocol (i.e., TCP, DNS, etc.)
Ed. Note 2: LAN traffic is in circulate mode, meaning a single computer with Wireshark can meet traffic between two other computers. If you want to run into traffic to an external site, y'all demand to capture the packets on the local computer.
Wireshark allows you to filter the log either before the capture starts or during assay, so you lot tin narrow down and zero into what you are looking for in the network trace. For case, you tin can fix a filter to encounter TCP traffic betwixt two IP addresses. Yous tin can ready it only to show yous the packets sent from one reckoner. The filters in Wireshark are ane of the principal reasons information technology became the standard tool for packet assay.
How to Download Wireshark
Downloading and installing Wireshark is easy. Step one is to check the official Wireshark Download page for the operating system you lot need. The basic version of Wireshark is free.
Wireshark for Windows
Wireshark comes in two flavors for Windows, 32 bit and 64 chip. Selection the right version for your Bone. The current release is three.0.iii as of this writing. The installation is simple and shouldn't cause any bug.
Wireshark for Mac
Wireshark is available on Mac as a Homebrew install.
To install Homebrew, you need to run this control at your Terminal prompt:
/usr/bin/cherry -east "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/principal/install)"
Once you have the Homebrew system in place, you can access several open-source projects for your Mac. To install Wireshark run this control from the Concluding:
brew install wireshark
Homebrew volition download and install Wireshark and any dependencies so it will run correctly.
Wireshark for Linux
Installing Wireshark on Linux can be a niggling different depending on the Linux distribution. If you lot aren't running 1 of the post-obit distros, delight double-check the commands.
Ubuntu
From a terminal prompt, run these commands:
-
sudo apt-get install wireshark -
sudo dpkg-reconfigure wireshark-mutual -
sudo adduser $USER wireshark
Those commands download the packet, update the package, and add user privileges to run Wireshark.
Red Hat Fedora
From a terminal prompt, run these commands:
-
sudo dnf install wireshark-qt -
sudo usermod -a -Yard wireshark username
The first command installs the GUI and CLI version of Wireshark, and the second adds permissions to use Wireshark.
Kali Linux
Wireshark is probably already installed! It's function of the bones packet. Check your menu to verify. Information technology's under the menu option "Sniffing & Spoofing."
Data Packets on Wireshark
Now that we have Wireshark installed allow's go over how to enable the Wireshark bundle sniffer and then analyze the network traffic.
Capturing Data Packets on Wireshark
When you open Wireshark, you lot see a screen that shows y'all a list of all of the network connections yous tin monitor. You also have a capture filter field, so you merely capture the network traffic you want to see.
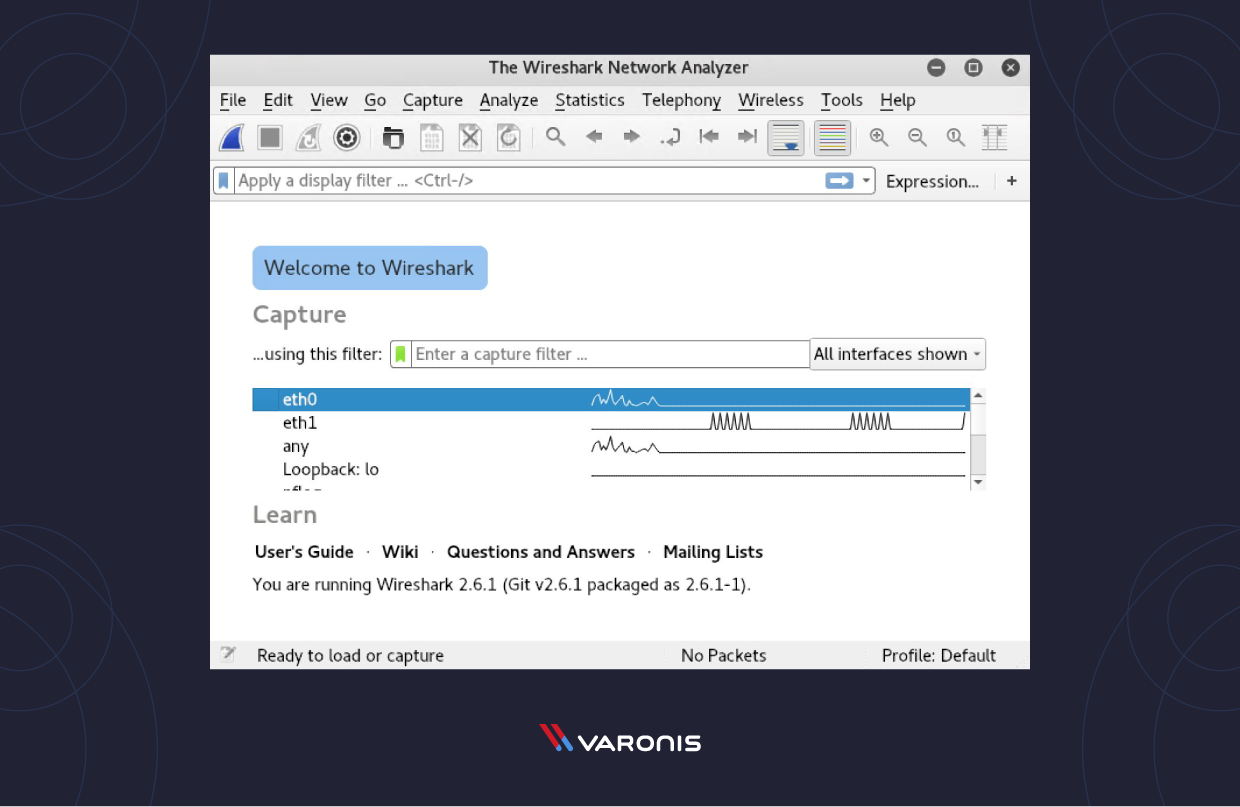
You can select one or more of the network interfaces using "shift left-click." In one case y'all accept the network interface selected, you tin start the capture, and in that location are several ways to do that.
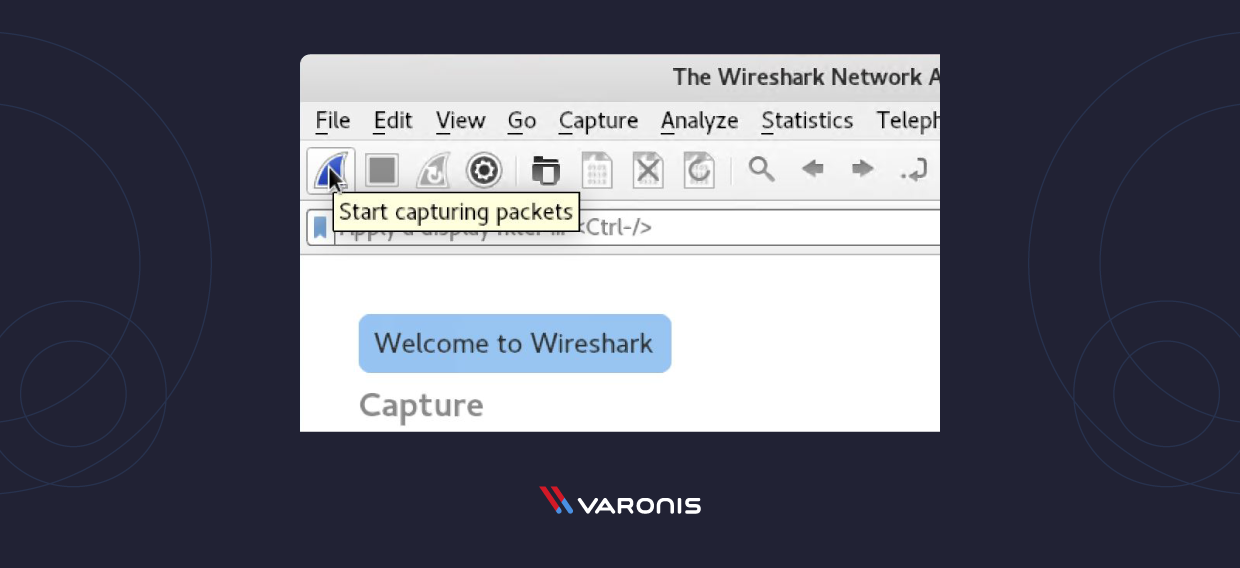
Click the first button on the toolbar, titled "Outset Capturing Packets."
You tin select the menu item Capture -> Start.
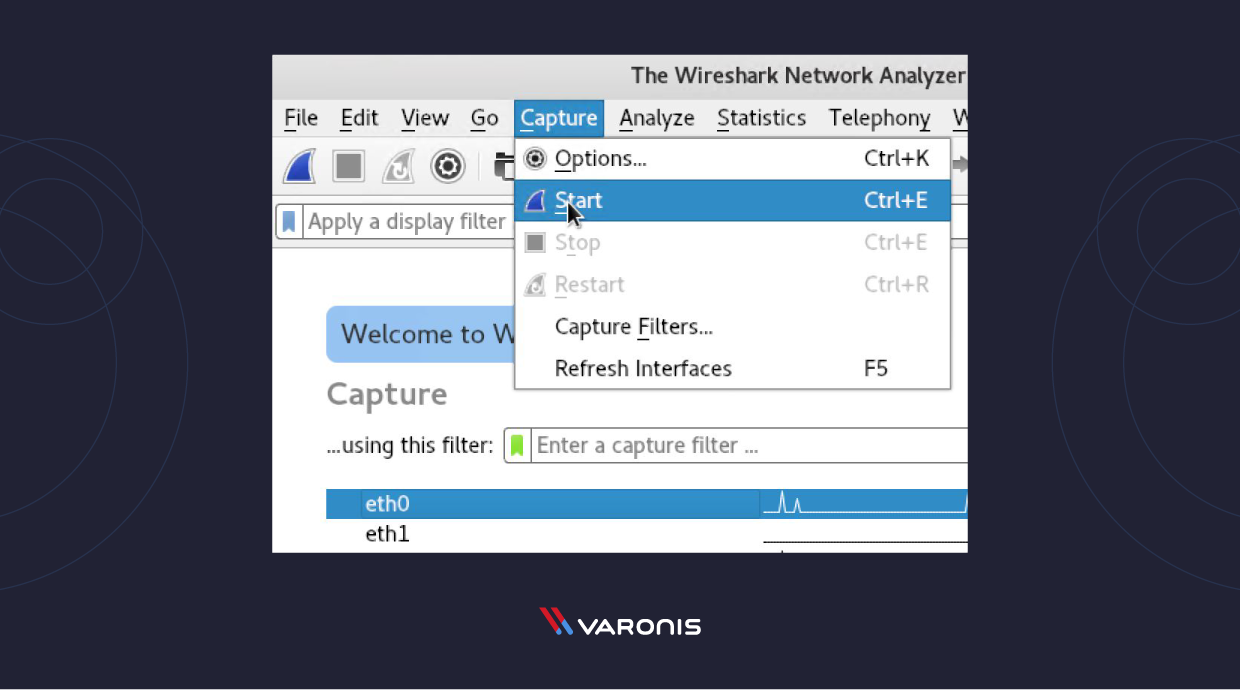
Or you could use the keystroke Control – East.
During the capture, Wireshark will show you the packets that information technology captures in existent-time.
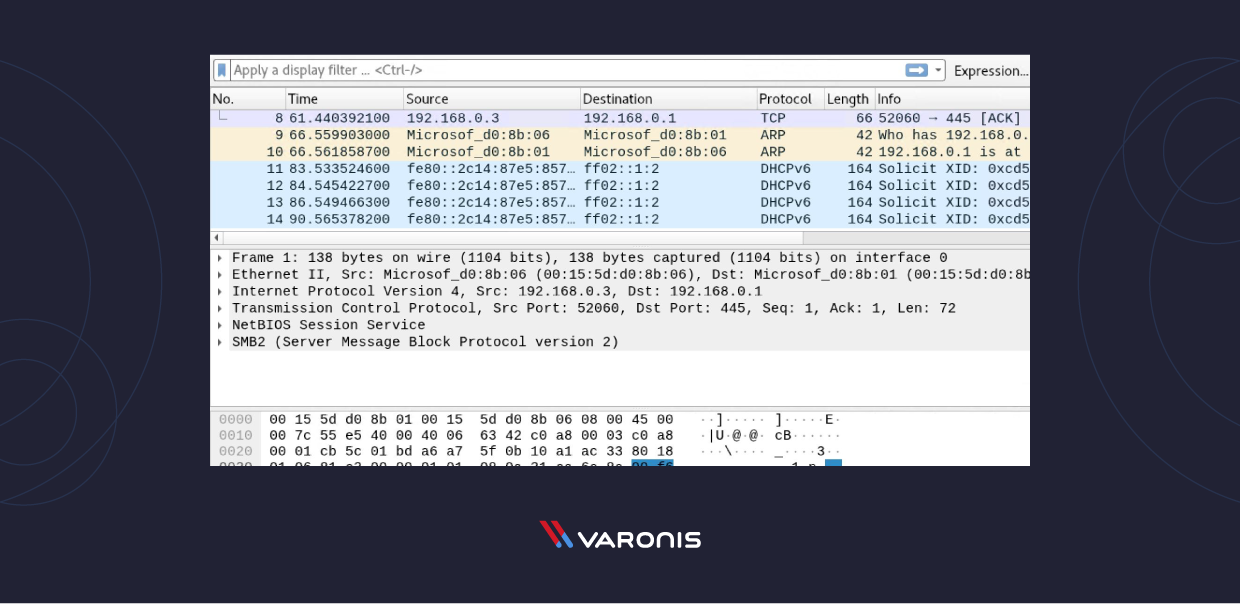
One time you have captured all the packets you lot need, you apply the same buttons or carte du jour options to stop the capture.
Best practise says that you should stop Wireshark bundle capture earlier you do analysis.
Analyzing Information Packets on Wireshark
Wireshark shows yous three different panes for inspecting packet data. The Parcel List, the elevation pane, is a list of all the packets in the capture. When yous click on a packet, the other two panes change to evidence you the details virtually the selected package. You lot can likewise tell if the packet is part of a conversation. Hither are some details about each cavalcade in the top pane:
- No.: This is the number order of the packet that got captured. The bracket indicates that this bundle is part of a conversation.
- Time: This cavalcade shows you how long after you started the capture that this packet got captured. You can change this value in the Settings menu if yous demand something different displayed.
- Source: This is the accost of the organisation that sent the packet.
- Destination: This is the accost of the destination of that parcel.
- Protocol: This is the type of packet, for example, TCP, DNS, DHCPv6, or ARP.
- Length: This column shows yous the length of the bundle in bytes.
- Info: This cavalcade shows you more than information almost the package contents, and will vary depending on what kind of packet it is.
Package Details, the middle pane, shows you as much readable information about the packet as possible, depending on what kind of packet it is. You tin correct-click and create filters based on the highlighted text in this field.
The lesser pane, Packet Bytes, displays the packet exactly as it got captured in hexadecimal.
When you are looking at a package that is part of a conversation, you tin right-click the packet and select Follow to see only the packets that are part of that conversation.
Wireshark Filters
One of the best features of Wireshark is the Wireshark Capture Filters and Wireshark Brandish Filters. Filters allow you to view the capture the way you need to see it so you can troubleshoot the issues at manus. Here are several filters to become you lot started.
Wireshark Capture Filters
Capture filters limit the captured packets by the filter. Significant if the packets don't match the filter, Wireshark won't save them. Here are some examples of capture filters:
host IP-address: this filter limits the capture to traffic to and from the IP accost
net 192.168.0.0/24: this filter captures all traffic on the subnet.
dst host IP-address: capture packets sent to the specified host.
port 53: capture traffic on port 53 only.
port not 53 and non arp: capture all traffic except DNS and ARP traffic
Wireshark Display Filters
Wireshark Display Filters change the view of the capture during assay. Later y'all have stopped the packet capture, yous apply display filters to narrow down the packets in the Packet List and then yous can troubleshoot your outcome.
The well-nigh useful (in my experience) display filter is:
ip.src== IP-address and ip.dst== IP-address
This filter shows you packets from one figurer (ip.src) to another (ip.dst). You can also utilize ip.addr to testify y'all packets to and from that IP. Here are some others:
tcp.port eq 25: This filter will bear witness you all traffic on port 25, which is unremarkably SMTP traffic.
icmp: This filter will evidence yous only ICMP traffic in the capture, nearly probable they are pings.
ip.addr != IP_address: This filter shows you all traffic except the traffic to or from the specified reckoner.
Analysts even build filters to detect specific attacks, like this filter to detect the Sasser worm:
ls_ads.opnum==0x09
Boosted Wireshark Features
Beyond the capture and filtering, there are several other features in Wireshark that can make your life better.
Wireshark Colorization Options
Yous tin setup Wireshark and so information technology colors your packets in the Packet Listing according to the brandish filter, which allows you to emphasize the packets you want to highlight. Check out some examples hither.
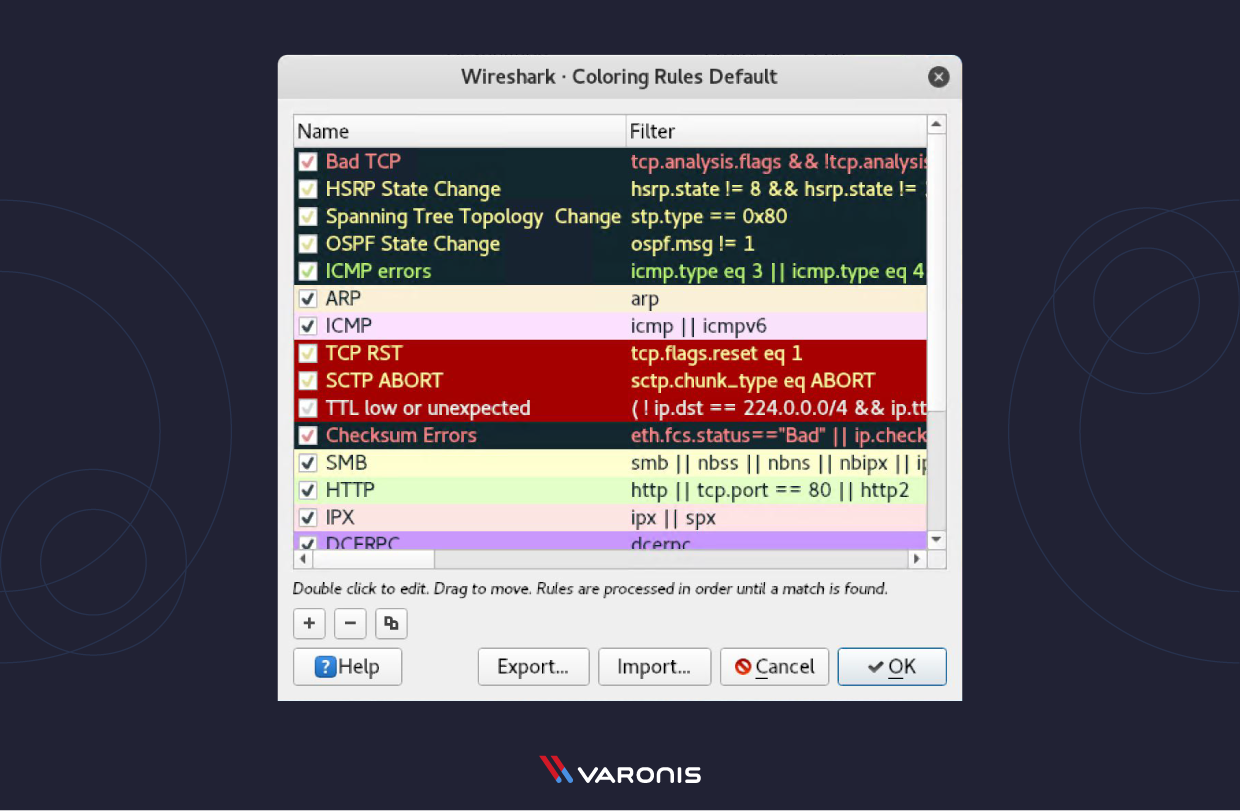
Wireshark Promiscuous Mode
By default, Wireshark only captures packets going to and from the estimator where it runs. By checking the box to run Wireshark in Promiscuous Fashion in the Capture Settings, you tin can capture near of the traffic on the LAN.
Wireshark Command Line
Wireshark does provide a Command Line Interface (CLI) if you operate a system without a GUI. All-time practice would be to use the CLI to capture and save a log so yous can review the log with the GUI.
Wireshark Commands
- wireshark : run Wireshark in GUI mode
- wireshark –h : show available command line parameters for Wireshark
- wireshark –a duration:300 –i eth1 –w wireshark. : capture traffic on the Ethernet interface 1 for 5 minutes. –a means automatically stop the capture, -i specifics which interface to capture
Metrics and Statistics
Nether the Statistics carte du jour item, y'all will detect a plethora of options to show details about your capture.
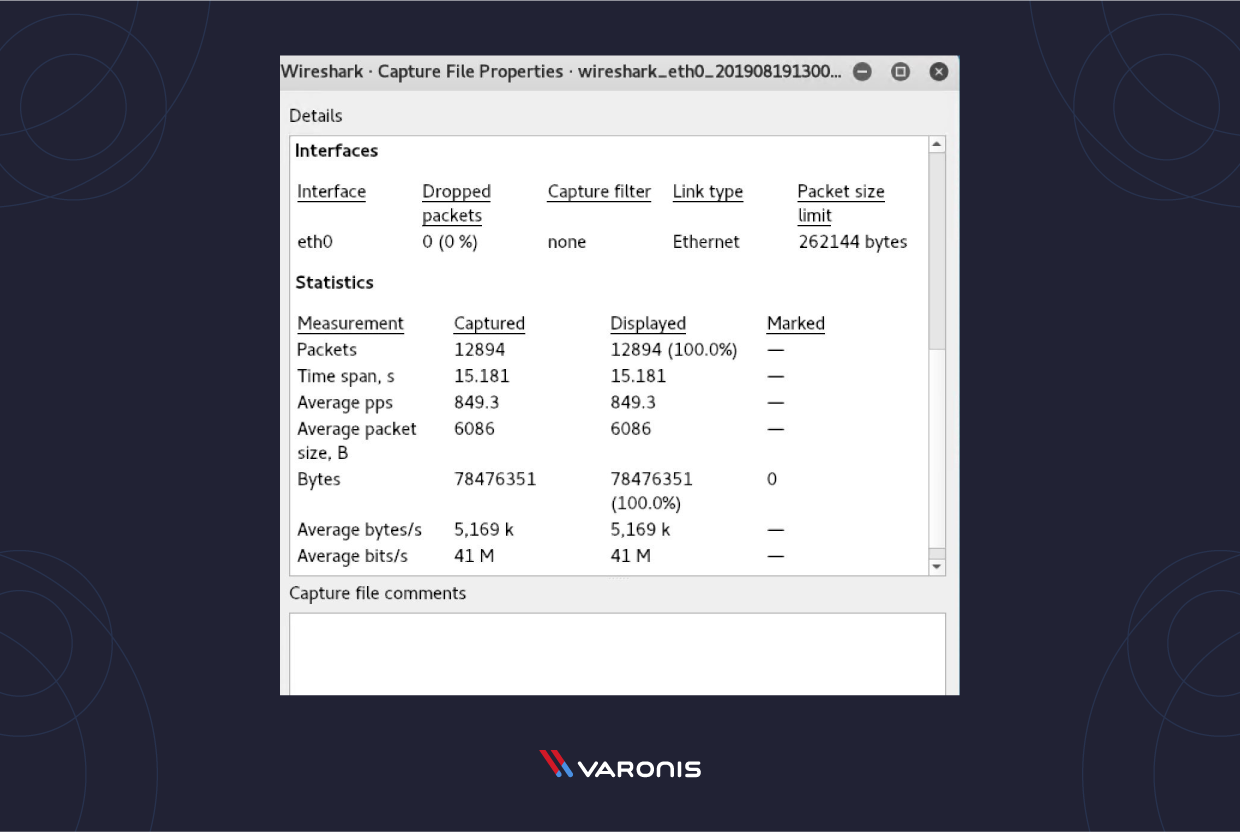
Capture File Properties:
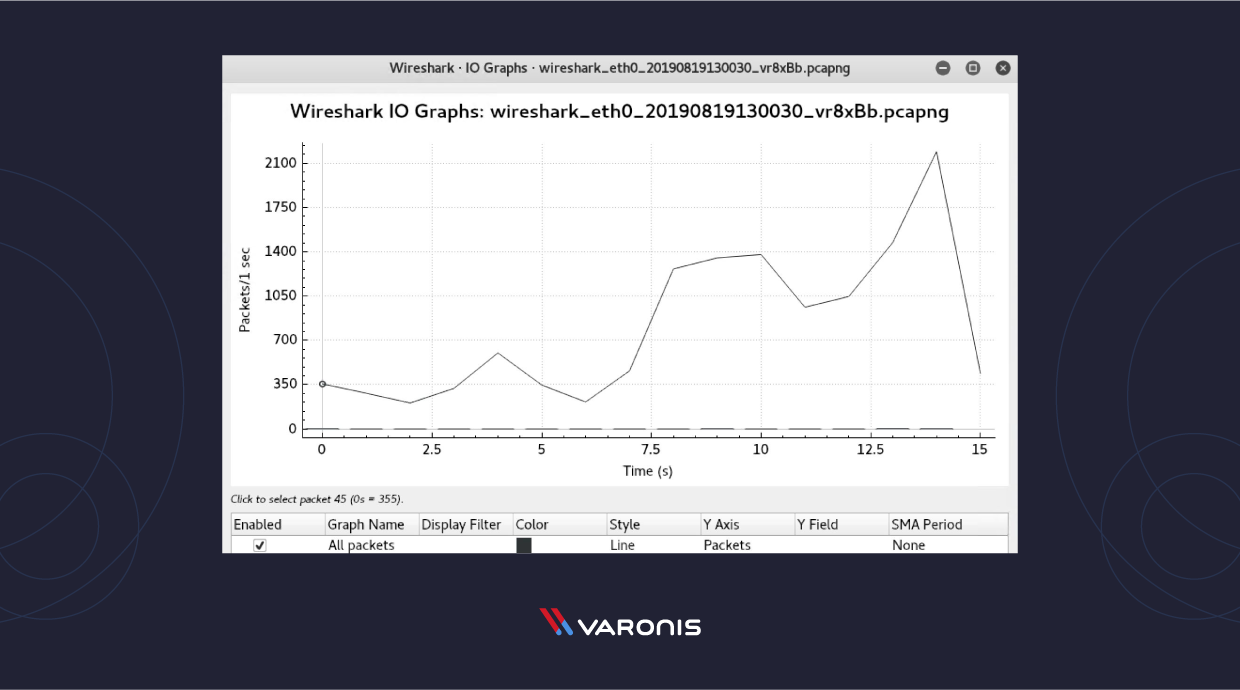
Wireshark I/O Graph:
Boosted Wireshark Resources and Tutorials
There are many tutorials and videos effectually that you lot testify you how to use Wireshark for specific purposes. Y'all should start on the principal Wireshark website and motility forward from there. You can find the official documentation and Wiki on that site.
Wireshark is a great network sniffer and analysis tool – even so, in my opinion, information technology's all-time used one time you lot know what you lot are looking for. You lot aren't going to use Wireshark to observe a new problem. In that location is as well much dissonance on the network. You need something like Varonis with Edge to brand sense of the overall state of affairs for y'all and point you to a threat to investigate, and then you use Wireshark to dig in deeper to understand exactly what is in the packets that are dangerous.
For instance, when Varonis Security Researchers discovered the norman cryptominer, they received an alert from Varonis pointing to suspicious network and file activity from several machines. During the analysis of the cryptominer, Varonis researchers used Wireshark to inspect network activities for some of the machines that were misbehaving. Wireshark showed the research squad that a new cyptominer, norman, was actively communicating to command and control (C&C) servers using DuckDNS. The Varonis squad was able to see all the IP addresses of the C&C servers the attackers used with Wireshark so the company could shut off advice and stopping the attack.
To see the Varonis team in action, sign up for a Alive Cyber Attack Demo. Choice any fourth dimension that works for you!
Source: https://www.varonis.com/blog/how-to-use-wireshark

0 Response to "Difference Between Uploading a Packet and Downloading Packet Wireshark"
Post a Comment